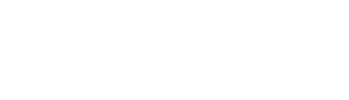: Integrated Protection
Technology, structure, and process converge at Ohms Law to create comprehensive protection for your digital life and assets. We ensure your information remains confidential and secure.
Discover Our Three Pillars
At Ohms Law, we are committed to providing comprehensive protection through our three-pillar approach: Technological Privacy & Security, Business Trust Structures, and Administrative Processes. Our focus on educational transparency empowers clients to make informed decisions. We believe in maintaining ongoing relevance in a rapidly changing digital landscape, ensuring our solutions are not only effective but also legitimate. Our dedicated team works tirelessly to integrate technology with legal expertise, creating a robust framework that safeguards your assets and privacy. Trust us to be your partner in navigating the complexities of privacy and security.
Our Integrated Solutions Provide Comprehensive Protection for Your Digital Assets
At Ohms Law, we understand that true protection requires a holistic approach. That’s why we’ve developed integrated solutions that combine technology, business structures, and administrative processes to provide comprehensive protection. Our approach ensures that all aspects of your digital assets are safeguarded against potential risks.
Technology Integration
We leverage cutting-edge technology to provide robust security measures, ensuring your data remains confidential and secure. Our solutions are tailored to meet your specific needs.
Business Structures
Our business trust structures provide a legal framework for your operations, protecting your assets and ensuring compliance. We offer expert guidance on navigating complex legal frameworks.

Administrative Processes
We streamline administrative processes to ensure compliance and efficiency, minimizing risks and maximizing protection. Our team of experts provides comprehensive support and guidance.
Strengthening Your Device Security with Expert Hardening
Ohms Law provides comprehensive device security hardening services to protect your sensitive data and prevent unauthorized access. Our experts employ industry-leading techniques to fortify your devices against evolving cyber threats, ensuring your peace of mind.
0
%
Reduction in potential vulnerabilities after our hardening process.
0
/7
Around-the-clock monitoring and support for your device security.
Enhance Your Network Privacy with Ohms Law's Expert Solutions
At Ohms Law, we understand the critical importance of network privacy in today’s digital landscape. Our specialized services are designed to provide robust protection against unauthorized access, data breaches, and other cyber threats, ensuring your sensitive information remains secure.
0
%
Client satisfaction rate with our network privacy solutions.
0
/7
Continuous monitoring and support for your network’s security.


Secure Your Communications with Ohms Law's Expert Solutions
In today’s digital landscape, secure communication is paramount. Ohms Law provides comprehensive solutions to protect your sensitive information. We offer messaging platform recommendations, security configurations, and contact verification to minimize data leaks and ensure privacy. Our approach integrates technology and legal expertise for robust protection.
- Messaging Platform Recommendations: Tailored advice on secure platforms.
- Security Configurations: Expert setup for maximum protection.
- Contact Verification: Ensuring secure and trusted communication channels.
Comprehensive Data Protection for Your Peace of Mind
At Ohms Law, we provide robust data protection services, including encryption, secure storage, and privacy-enhancing configurations. Our goal is to prevent data leaks, secure sensitive information, and establish proper data handling procedures to safeguard your business.
0
%
Reduction in potential data breach incidents with our solutions.
0
%
Compliance with data protection regulations achieved through our services.